6,626 total views, 4 views today
Email has many advantages, but there are also problems that we should be aware of. The main threats come from malicious actors who attempt to compromise email systems with phishing attempts, malware, ransomware, and other threats.
Email security measures are always being improved in order to safeguard both recipients and senders.
Any firm needs email security, but companies that send emails to big recipient lists especially need it. And as the sender, you must take precautions to guarantee the security of every email you send.
This article will define email security, explain why it’s crucial, and explain how to make sure your emails are safe.
Email security: What is it?
The procedures and strategies used by email service providers (ESPs), senders, and recipients to protect themselves and other people against unauthorized access and malicious assaults are collectively referred to as email security. These attacks often aim to profit by stealing data or causing trouble for a business.
What makes email security so crucial?
Email’s accessibility as a means of information sharing and communication is one of its advantages. However, this also makes email susceptible to threats. With access to your mailbox, an attacker can discover a lot of private information about you or your company and use it for evil.
The sender reputation and trust you’ve built as a company may also be used by malicious individuals to send bulk phishing emails.
Because it helps safeguard both your information and those of your customers and business partners, email security is crucial.
Do you want to know how frequent email attacks are? Let’s examine some figures:
- The top 2 methods used by malicious actors to infiltrate organizations are web applications and email (Verizon).
- 35 percent of ransomware cases use email (Verizon).
- Malware is most frequently delivered via email (Verizon).
- In 86% of organizations, phishing emails caused at least one person to click on a dangerous link (Cisco).
- Around the holidays, phishing typically reaches its height, rising by 52% in December (Cisco).
Here’s the good news: You may increase the security of your emails by using authentication techniques and other safeguards. Next, we’ll examine your options for enhancing security.
Email security recommendations
Protecting your firm and its recipients from data breaches and other dangers starts with securing your email correspondence. To make sure that your company email exchanges are secure, adhere to following best practices.
1. Employ safe login and authentication techniques
A simple password won’t provide you with the security you need to safeguard both your company and your recipients after you log into your business accounts. To keep your emails and data secure, utilize one of the following login authentication strategies throughout your firm.

Using two factors to authenticate
The user must combine two different types of authentication factors in order to use two-factor authentication (2FA). These elements can be divided into 3 groups:
- Factors of knowledge (something you know, like a PIN or password)
- possessive aspects (something you have, like a debit card or mobile phone)
- Intrinsic variables (something inherent to you, like a fingerprint)
For instance, to use an ATM, you must display your debit card and enter your PIN (the possession factor) (knowledge factor). This kind of authentication frequently uses time-based one-time passwords or SMS (text) messages. Find out more about 2FA.
Solitary sign-on
Users can access numerous applications using single sign-on (SSO) after authenticating their identities with an identity provider. This is frequently used in conjunction with 2FA.
In addition to making login simple for the user and aiding in the enforcement of strong passwords, centrally managed access lowers the possibility of account penetration. SSO also makes it simpler for groups to safely store and distribute login information for tools like ESPs. Find out more about SSO’s benefits to account security and how to configure it for SMTPServer.
Using API Key
Alternatives to username and password logins that are more secure include application programming interface (API) keys, which are distinct codes that identify and authenticate a person. This technique is frequently used by developers to restrict access to an API, such as an email API.
You can limit access to certain parts of your account by choosing various levels of scope or permissions for each user when you set up an API key. By doing this, you can restrict who can see client data, which we’ll talk about later.
Find out more about the various degrees of access and using API keys to connect to SMTPServer’s services.
2. Establish sender authentication guidelines

By using sender authentication methods, you may prove to inbox service providers (ISPs) that you are a trustworthy sender and not a spammer or spoofer. Additionally, these protocols make it more difficult for phishing attempts to be sent by malicious actors pretending to be your company or to be you.
On the other hand, if you don’t have these rules in place, you leave yourself vulnerable to spammers or fake accounts attempting to profit from your reputation. Your reputation could suffer as a result of this, and you might even find yourself on a blocklist.
Senders should utilize the following authentication protocols:
- The Sender Policy Framework (SPF), which aids in determining which mail servers are authorized to deliver emails from a specific domain
- DKIM, which confirms that the email sender is accountable for both the email’s content and the domain from which it was sent,
- DMARC, which enables senders to designate how to handle emails that are not validated using the 2 techniques above, is a domain-based message authentication, reporting, and conformance system.
3. Utilize an SMTP server
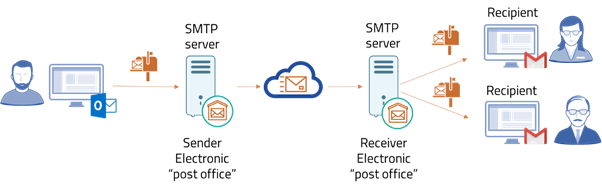
In essence, the pipeline that carries your emails from your server to the recipient’s inbox is called Simple Mail Transfer Protocol (SMTP). Your email is processed by an SMTP server, which also determines which server it should be sent to. The message is subsequently downloaded from the server by the receiving ISP and delivered to the recipient’s inbox.
An SMTP server serves as the first line of defense in defending recipients from fraudulent senders by verifying that the email is from an active account in addition to forwarding it to its intended recipient.
By requesting that you log in using a server-supported authentication method, SMTP authentication aids in the security of your outgoing email as a sender. Through SMTPServer, find out more about SMTP authentication.
4. Use encryption to safeguard data

One of the best ways to safeguard the content of your emails is encryption. This is crucial if you send emails to recipients that include sensitive information about them.
Our introduction to encryption is a wonderful place to start if you’re just getting started. But in essence, encryption encrypts data in emails so that only users with the proper permissions—typically the sender and the recipient—can read it.
Data is shielded as it moves from your server to the server of your email provider thanks to Transport Layer Security (TLS), a sort of encryption. If the recipient’s email server supports it, SMTPServer will by default try to transmit your emails over a TLS-encrypted connection. By doing this, malicious parties who use passive surveillance equipment along the road are prevented from accessing the email content.
Find out more about the encryption used by SMTPServer to safeguard emails.
5. Limit data access
Data access should only be granted to staff who truly require it, especially when it comes to recipients’ data. As a result, there are fewer possibilities that an email security failure will result in a wider data leak. There are several methods for doing this:
Only allow employees who frequently require access to your ESP to have user seats. Then, periodically audit user seats to make sure inactive users are removed.
Establish separate permission levels according to each user’s role to give each team member access to the tools they require to do their jobs while safeguarding confidential client information. Through the Teammates feature of SMTPServer, users may specify the permission levels for several team members who share an account.
First-party data is more significant than ever as we progress toward a cookieless world, making it the responsibility of every company to safeguard the information that customers have trusted them with.
6. Inform staff members about cybersecurity

At your company, you have probably sat through a few cybersecurity training courses. And even though they could seem repetitive or overflowing with obvious information, these are crucial for maintaining the security of your company.
You might be an expert at spotting phishing emails if you send emails. To safeguard your company and your clients, however, you need everyone in your corporation to be equally as smart.
By frequently educating staff members on how to spot and avoid cybersecurity dangers, you can help safeguard your company while also arming them with the information they need to safeguard themselves.
Utilize SMTPServer to send safe emails
Protecting your data (and the data of your clients) is SMTPServer’s top priority. Devoted compliance and delivery teams, TLS encryption, secure data centers, and operational security standards that limit access to client data are just a few of the security precautions we put in place. Find out more about how SMTPServer protects the privacy of your emails.
Are you prepared to send secure emails? Try SMTPServer without cost.